What if we could massively improve your security posture..?
Let’s Introduce Zest
ZEST is a sophisticated full-stack vulnerability scanner and security management application, built utilising the OutSystems platform.
ZEST delivers a comprehensive and tailored approach to vulnerability management by allowing users to pick from a suite of pre-installed and configured tools or to integrate their own while retaining a unified reporting scheme.
Green Lemon Company
ZEST Elevates Your Security Posture
AI Augmented Security, So What?
Bespoke Scanning
Optimise app scanning clusters
Use tools you trust, and deploy new tools from the dashboard. Assign specific clusters of scanning tools on an app-by-app basis to optimise your scanning capability and protection.
Scan Frequency
Automated scan cadence
Meet any combination of scanning standards by creating routine scanning for each application on a needs basis. The dashboard allows you to customise scanning cadence in a click.
Reporting
Act on good information
The use of super-accurate reporting allows customers to act on issues in the correct order of priority whilst increasing awareness and scaling risk mitigation actions for the security team.
Integrated
One screen to rule them all
Ground-breaking use of advanced AI modelling wrapped in a powerful back-end dashboard gives security teams and management a holistic application to cover the entire estate.
Safer
Reducing cyber incidents
Zest reduces incidents by providing early vulnerability identification, exception reporting and preventative remediation, only possible by integrating tools and automating scanning cadence.
SBD
Security by Design
Integrate Zest into your development platform and CI/CD to establish SBD as your development/deployment security method. Zest scans during any cycle as well as pre-deployment.
Let’s Take a Good Look at Zest
Key Features
ZEST seamlessly integrates into both the software development lifecycle (SDLC) and continuous integration/continuous deployment (CI/CD) pipelines, fostering a security-first approach throughout development. By embedding security checks at every stage, ZEST ensures that proactive measures are prioritised over reactive responses to potential breaches.
ZEST offers flexible scheduling for vulnerability scanning, supporting instant, one-time, or routine security assessments. Its advanced, user-friendly scoring system evaluates application risk profiles to optimise resource allocation, focusing scanning efforts where they are most needed while minimising unnecessary overhead.
Leveraging AI, ZEST enhances vulnerability management by normalising data, prioritising vulnerabilities, and identifying relationships between them. This AI-driven approach not only increases the efficiency of vulnerability identification but also reduces false positives, allowing security teams to concentrate on critical issues.
Beyond systematic scanning, ZEST enables the scheduling of penetration tests and the configuration of social engineering exercises. These features help assess both human and technological assets, ensuring that your entire digital landscape remains as secure as possible.
Key Features
Centralised security management: A one-stop solution to monitor and increase the security posture of all applications and assets from a unified interface.
Easy configuration: Configure one or a group of applications, for one time, or repeated scanning.
Fully customisable: Pick and choose the tools you want to be part of your assessment.
Simple reporting: Gauge the security of your assets with an advanced scoring system
Full stack scanning: Comprehensive vulnerability scanning that covers Web applications, SAST & DAST, API’s, infrastructure and more.
Custom scanning: Have your own or preferred tools? Integrate them into ZEST to align with your requirements.
Hosting: On-Cloud, or on Premise.
AI Enhanced: ZEST uses the power of AI to reduce false positives, normalised reporting, and prioritise vulnerabilities based on related vulnerabilities.
Find and Fix: Built in remediation workflow to proactively address vulnerabilities and schedule rescanning to validate the patches.
Schedule and relax: Schedule scans or conduct manual penetration testing with experts through a single interactive page allowing the evaluation of security measures through simulated cyber-attacks.
Social Engineering: Create social engineering scenarios to train and educate human assets on simulated phishing exercises.
Keep Informed: Live threat feeds to stay informed about the latest security threats and developments.
Key Benefits
Benefit from a centralised platform that offers comprehensive security oversight, allowing you to monitor and enhance the security posture of all applications and assets from a unified interface.
Achieve ISO 27001 compliant standards by easily configuring scans for groups of applications and assets, enabling instant, scheduled, or recurring assessments as needed, providing flexibility and convenience in managing security assessments.
Comprehensive vulnerability coverage to ensure all aspects of digital assets are thoroughly assessed for vulnerabilities with: Web App, SAST, DAST, API and Infrastructure scanning.
Leverage AI-driven reporting enhancements to streamline analysis, reduce false positives, and prioritise vulnerabilities. Proactively manage vulnerabilities with a remediation workflow that facilitates prompt mitigation and scheduled rescanning for remediation validation.
Swiftly schedule manual penetration tests to evaluate security measures through real-world cyber-attacks, identifying and addressing vulnerabilities before they are exploited in the wild. Additionally, create social engineering scenarios to raise security awareness among employees and mitigate the risk of successful social engineering attacks.
The solution offers flexibility in deployment options, allowing organisations to choose between on-premises, cloud-based, or hybrid solutions. This flexibility enables organisations to deploy the solution in a manner that best suits their infrastructure and security needs. - Customise assessments with the ability to pick and choose different tools and scan templates to align precisely with requirements and conduct different types of security evaluations, ensuring a tailored approach that addresses specific vulnerabilities and compliance standards. (edited)
A selection of the ZEST application screens…

New ZEST Pentest

My Applications Page

Remediations

ZEST Dashboard

Assessments

ZEST Report - Monthly
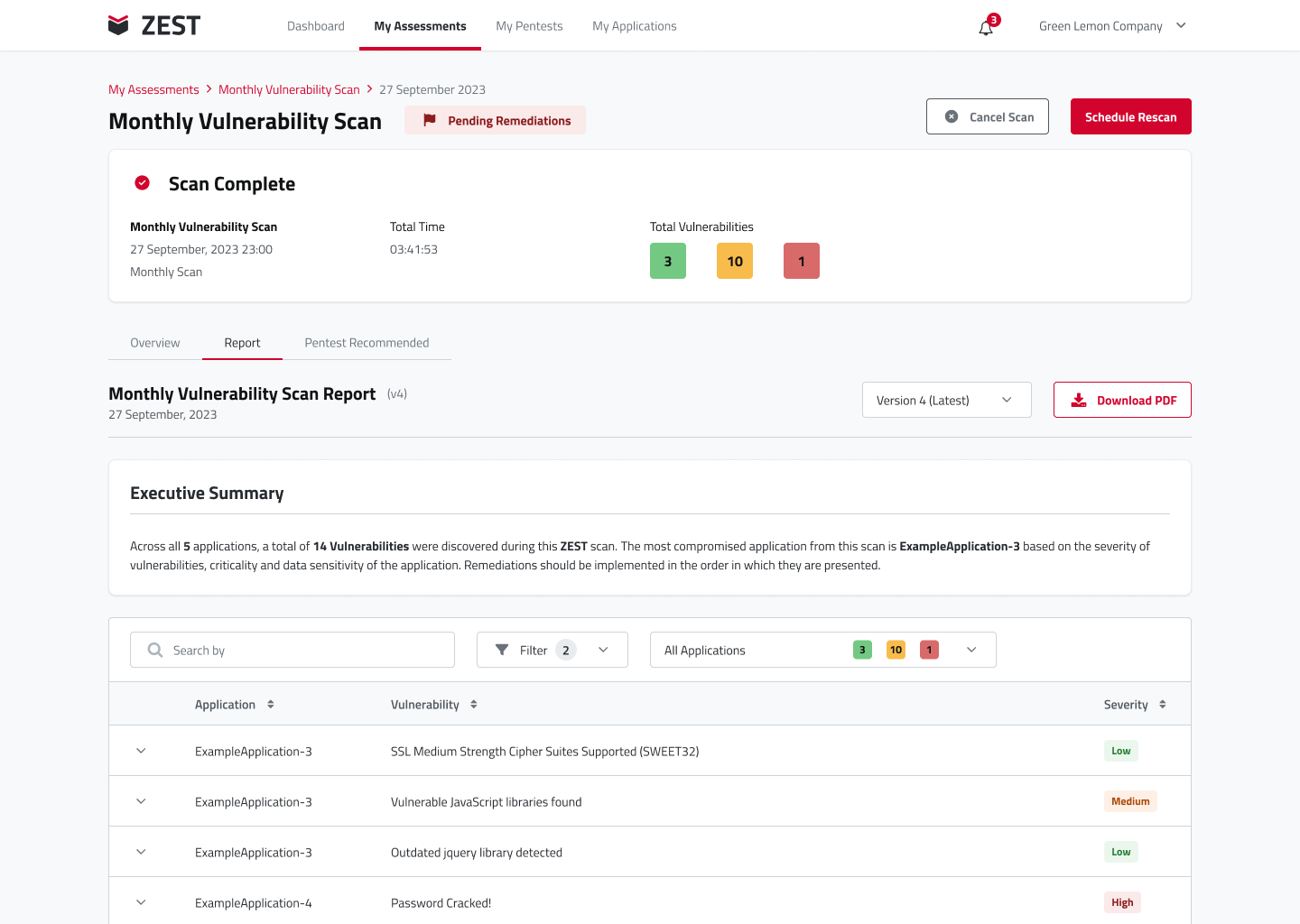
Pending Remediations Report







